Executive Summary
In most financial planning firms today, nearly all business operations depend on some form of cloud-based technology or other data storage system. And given the sensitive and personal nature of client information that financial advisors are entrusted with and work with on a daily basis, reliable security measures need to be implemented to protect that client data, wherever it is stored. In fact, both the SEC and FINRA have increasingly recognized the significance of cybersecurity measures for financial planning firms in recent years, and offer extensive regulations, rules, and guidelines to ensure advisors effectively protect client and firm data against the vast expanse of malicious cyber-threats that attempt to steal valuable Personally Identifiable Information (PII) across the globe on a daily basis.
However, the rules and regulations around cybersecurity and identity theft can seem overwhelmingly complex to deal with, especially for financial planners who are sole proprietors or who work in smaller firms. As while larger firms have the staff infrastructure of dedicated IT and compliance teams, smaller practices don’t have this option and are often left to their own devices (or seek out consultants at additional compliance cost) to develop cybersecurity plans for their practices.
Even more problematic, though, is simply the fact that most financial planners became financial planners to be financial planners… not cybersecurity experts. And while most financial planners may know enough about computer systems and basic internet processes to manage their firms, few have an extensive background in IT sufficient to fully develop their own sound, yet manageable, cybersecurity plan.
In this guest post, Preeti Shah – herself the founder and sole proprietor of Enlight Financial, an RIA located in Matawan, New Jersey that works with physicians and business owners – shares her own 16-point cybersecurity plan that she personally developed, and how she boiled down the complex regulatory requirements of cybersecurity into practical categories of tools and systems to manage and implement on her own.
In practice, Preeti converted her cybersecurity requirements into a comprehensive checklist that includes measures to protect her email systems, ensure safe mobile technology practices, provide secure document storage and software solutions for use with her clients, maintain a secure physical working environment, and provide for an emergency plan in case disaster strikes.
Ultimately, the reality is that no cybersecurity plan will be perfect as cyberthreats continually evolve. Still, though, a work-in-progress framework that continues to evolve as each point is revisited and improved upon over time can help protect key data and demonstrate to regulators a good-faith effort to do so. And the reality is that financial advisors don’t need to be cybersecurity experts to implement a reasonably sound plan to better protect their clients’ and their firm’s confidential data… at least once their cybersecurity requirements are boiled down to more practical steps that can be implemented!
Cybersecurity and identity theft have become increasingly prominent areas of concern not only for the general population but also for financial advisors, especially, who deal with sensitive, personal client data day in and day out. The potential worries and precautions that must be taken are manifold, as both the SEC and FINRA have become increasingly stringent in their own requirements of what financial advisors are expected to do in order to protect their private client information.
The caveat, however, is that most advisory firms are solo practices or consist of only a few financial advisors banded together as partners, whose primary focus is on serving clients… not being IT experts trying to interpret ever-lengthening cybersecurity requirements from regulators! Fortunately, though, there are plenty of relatively straightforward safeguards that financial advisors can take to prevent the potential nightmare scenario of getting hacked and having to send out the dreaded email explaining a breach to clients.
In facing this challenge in my own advisory firm as a solo practitioner, I tried to break down the regulatory requirements of cybersecurity for financial advisors into a checklist of practical actions and safeguards I could implement myself, both to protect my clients’ information and to be able to show regulators the steps I was taking to do so.
In the hopes that it is helpful to other financial advisors trying to figure out what to actually do with respect to cybersecurity requirements (when we’re not ourselves technology experts), I present my own 16-point cybersecurity plan for the areas I was looking to tighten and address:
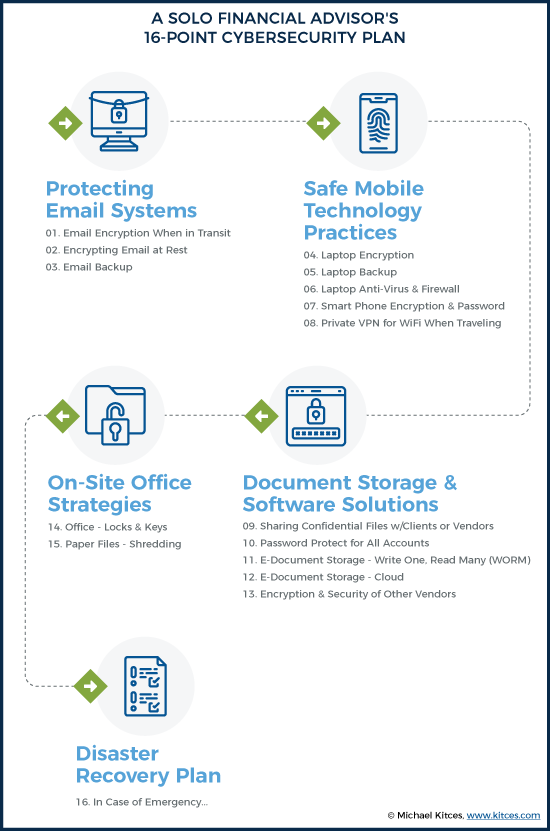
It was a long, daunting list at first, but it also helped me to crystallize the requirements needed to address each step and formulate a solution that worked for me. Keep in mind that each advisor’s technology stack is unique to meet the needs of their own business structure, and so might differ from mine – there are often multiple vendors, services, software, and methodologies that can be used to address each of these different points.
Email Solutions
I use Microsoft Exchange via an Office 365 online subscription for my email, for which I pay $20 per month. It provides several features that secure email both in transit and stored in the cloud, as well as backup data.
1. Email Encryption When In Transit
Transport Layer Security (TLS) is a Microsoft Exchange Office 365 feature that encrypts information as it is being ‘transported’ through email.
While TLS is automatically enabled as part of the Exchange service, I also manually installed Azure Rights Management, a free plug-in proprietary to Microsoft, as an additional layer of encryption protection. It’s less commonly used than TLS, and therefore possibly more difficult to hack.
In order for outgoing email to be encrypted by Azure Rights Management, I just need to insert the word “Encrypt” in the subject line of emails. In addition to encrypting the information, it also allows the option to require recipients to verify themselves and enter a password to open the message, although I haven’t enabled this feature because I think my clients would find it too much work and I am careful to only send to known email addresses of clients in the first place.
In addition to using these features, I refrain from including any Personally Identifiable Information (PII) in emails such as Social Security or bank account numbers. However, I will sometimes list the client’s address in an email when confirming things like a move; even though home addresses are considered PII, such information is usually available publicly on the internet so I am not quite as cautious with it – I use my judgment as appropriate.
2. Encrypting Email at Rest
Microsoft Exchange stores everything in the cloud using BitLocker 256, which, as the name implies, uses 256-bit encryption to protect files. While new emails I receive are stored locally for a short period on my laptop, they get backed up and encrypted to the cloud every time an Exchange backup is run. The BitLocker 256 technology meets FINRA’s industry standard for strong encryption, defined in FINRA Regulatory Notice 10-59 as “256-bit or higher encryption”. There is some debate about whether full 256-bit encryption is required for SEC-registered investment advisers (as opposed to broker-dealers under FINRA), and state-registered investment advisers may have their own state-level requirements. To be safe, I strive for 256-bit encryption wherever I can.
3. Email Backup
I run a manual Outlook .pst file backup every few weeks and keep the backup files stored on my laptop (which is also backed up to the cloud). This is in addition to the email backup carried out by Microsoft Exchange (which is done automatically and included as part of the subscription). A software program like Backupify would automate the process but, for my purposes, the manual backup and automatic Exchange backup are sufficient.
Safe Mobile Technology Practices
4. Laptop Encryption
Although I had hoped to use Bitlocker, it is unfortunately not available on Windows Home 10. VeraCrypt is one that people use, but it’s freeware, and I’m concerned that it doesn’t seem to be backed by a proper company. I am currently looking into McAfee Complete Data Protection as a potential solution. This will enable me to encrypt all my laptop files automatically and usually involves a second password in order for me to view my files unencrypted.
5. Laptop Backup
I currently use Carbonite, which provides cloud storage services and 128-bit encryption for $100 per year. The company will mail a backup of my files to me if I need them to, and they are relatively easy to reach.
While I could upgrade my subscription for their 256-bit encryption service, the annual price is steep, at $700; instead, I’m looking at encrypting my laptop files (as noted above) and then having those already-encrypted files stored through Carbonite.
6. Laptop Anti-Virus and Firewall
I have McAfee enabled to provide both firewall and anti-virus protection. While firewall protection will protect against hackers from accessing my system, anti-virus protection is also important to prevent any malicious programs that can be picked up from websites or emails from infecting my machine. My biggest task here used to be remembering to keep the software updated through upgrades, but I turned on the automatic upgrade feature so it no longer asks me to manually agree to it. Now my anti-virus system stays fully up to date!
7. Smartphone Encryption and Passwords
While fingerprint scanning would seem like a foolproof method to lock my iPhone, I’ve found the technology often doesn’t work on my phone so I simply rely on a strong numeric password lock to keep my phone encrypted when not in use.
Notably, I try not to keep private client information on my phone in the first place. However, while my iCloud account doesn’t store my Outlook email, or my personal Gmail and Hotmail emails (since my iPhone just connects to them in real-time), it does store my Outlook contacts (since I enable Outlook Calendar) and the contacts that I enter into my phone directly. Since there’s a possibility that someone might try to access my client emails through the phone, I keep what’s on the phone itself encrypted and restrict access with a strong password while I try to figure out how to further limit what syncs from Microsoft Exchange and Salesforce (my CRM).
8. Private VPN For WiFi When Travelling
I go to India every summer and travel quite a bit, so I pay for NordVPN for about $60/year, a private VPN service in Panama widely reviewed on PC World and other sites, which allows me to connect securely to another network over the internet. I prefer a VPN outside the US that doesn’t necessarily track its users and that can provide subpoenaed data (an unlikely scenario, but I still don’t like the idea). NordVPN is in Panama and doesn’t track anything, has 60 servers around the world, and the connection is supposedly fast. I don’t always have it on when I am working from my home office; I use it mostly when I travel.
Document Storage and Software Solutions
9. Sharing Confidential Files With Clients And Vendors
In addition to using eMoney for financial planning, I also use the eMoney Vault to ask clients to post sensitive info (as eMoney takes its own data security very seriously), or I allow the client to choose a method if they prefer Dropbox or something else (but caution them that their own solution may not be as secure as eMoney). Alternatively, I will password-protect a document using WinZip if I know the client is not tech-savvy and call them with the password.
10. Password Protection For All Accounts
I chose LastPass based on several suggestions from others in the XY Planning Network, and have been using it to store all of my passwords ever since. It generates unique passwords so that I am not using the same ones across different websites like eMoney, TD Ameritrade’s Veo custodial platform, Morningstar, etc.
11. EDocument Storage – Write Once, Read Many Times (WORM)
These days I use DocuSign through TD Ameritrade’s custodial platform so I’m mostly paperless, but I do have some paperwork and contracts from my first few clients. I want to be 100% paperless, but during my old Broker-Dealer days I was told that I had to use something called WORM (Write Once, Read Many) storage in order to be able to do that. In other words, the original cannot be editable (“Write Once”), even if it’s referenced frequently in the future (“Read Many”) for audit purposes. While WORM standards don’t necessarily apply to non-Broker Dealer affiliated RIAs like me, I like to play it safe and follow the protocol.
There are WORM-compliant cloud storage systems, but I just haven’t had the time to look into this, especially since I’m a Sole Proprietor trying to balance a manageable number of clients. So, for now, I just keep my one locked drawer of client paper files, to have available in case of an audit. I figure eventually I’ll have to re-sign old contracts with clients, and since they will all have originated in DocuSign, I’ll automatically transition to become paperless over time.
12. EDocument Storage – Cloud
As mentioned, I am a Sole Proprietor with no assistant. Since it’s just me, I’m able to manage by keeping files on my laptop – no one else needs to access them. If I do hire someone, I would probably use Box.com, which offers compliant services for financial advisors to store files.
13. Vendor Encryption And Security – CRM/eMoney/Erado/Other Vendors
I use Salesforce mainly to enter client info like Social Security, birthdays, etc., and eMoney has account information and connections to client accounts (for account aggregation purposes). I also use MessageWatcher, which protects information that I email through LinkedIn, and Erado for its website archiving services. MyRepChat offers a compliant text-messaging platform that allows texting to clients and mass text messages to contacts. Both MessageWatcher and MyRepChat programs were offered at a discount for members of the XY Planning Network.
Fortunately, industry vendors such as these typically follow recognized security standards themselves, most commonly SOC2 (a reporting framework developed by the AICPA to assure systems are set up with appropriate standards addressing security, privacy, and confidentiality). For most of the vendors I use, I was simply able to find information on their websites about their cybersecurity policies and how my clients’ PII data would be treated.
As mentioned in the email backup section (point #3) above, I do manually backup my email from Outlook because it is my most important data source and Outlook makes it easy. However, I don’t separately backup Salesforce or eMoney or other vendors, as I trust the backup processes they run automatically.
On-Site Office Strategies
14. Office – Locks and Keys
I work out of my home so this is not so much of an issue now. But when I have someone visit, I try to keep my file cabinet and even office locked. My home office could be visited by an auditor at any time, and I can’t have someone opening the door, letting themselves in, and having client data out in the open.
15. Paper Files – Shredding
It goes without saying that I shred everything with client info on it when I no longer need it. My shredder sits right under my desk.
Disaster Recovery Plan
16. In Case of Emergency…
Per FINRA requirements, I have a plan in place for Disaster Recovery which involves a list of all vendors to call, as well as passwords and account info, client info, processes to follow, and more. The rest of the plan mostly relies on me having backups for everything and being able to restore my email, laptop, files, and texts virtually if something were to happen to my physical location and equipment.
Also, because I am a Sole Proprietor with no assistants, in case something happens to me, I have designated my brother to call clients, vendors, the state/FINRA, and other relevant third parties to let them know I will be temporarily unavailable, or in case of tragedy, not coming back. I still need to give him personal Power of Attorney as well so he can disperse money to pay bills and take care of business on my behalf. He doesn’t have access to my passwords or client data now; I’ve simply given him the password to my laptop, the location of important data, and the recovery plan document.
If my laptop is destroyed along with me, perhaps in an accident, my information is mostly available in the cloud, but I don’t yet have a plan for how he would get all the cloud passwords since I’m not sure how to get him the information without giving access to him now. I’m still working on making this foolproof.
Phew, a large and overwhelming list, right? Rest assured that a good cybersecurity plan is not set up overnight and may take several months to complete. And once a plan has been established, a good maintenance process will ensure that all systems are working smoothly as intended on an ongoing basis with minimal effort.
This might be as simple as setting up an automatic quarterly or annual recurring task in Outlook. I have reminders to check that backups are actually happening, information is being archived, and services are still compliant. For example, in my Tasks List in Outlook, I have a category labeled “Compliance” where I have created a quarterly task for me to check MessageWatcher to ensure my emails are being archived properly. Each time I get this reminder, I find a few randomly selected emails to check that they were indeed archived. I have similar quarterly reminders to do the same for my Carbonite backups, where I check that all the files and folders I specified are indeed being backed up, and another to check the cloud to confirm that all my business files are being backed up. Once I complete these tasks, I make a note in each Outlook Task item that the check was done, hit Complete, and the Tasks automatically re-generate a new deadline for the next quarter.
Even though my cybersecurity plan is still a work-in-progress – as I’ve mentioned, there are more than a few areas that I’m still hammering out – simply having all the areas of concern listed in one place has helped me better visualize how everything needs to come together and how I am addressing each point. And when possible, I try to automate and make everything as simple as possible!


Leave a Reply