WEEK IN IT SECURITY – Just as we were reporting last week on our sister site The Evolving Enterprise that ransomware is behind 1 in 3 cyber security attacks on organisations, news was breaking of another major ransom attack, reports Jeremy Cowan.
This time South Carolina-based Blackbaud, a third-party supplier of database services and customer relationship management (CRM) systems for enterprises, had paid hackers an undisclosed ransom to unlock its own client data.
Blackbaud describes itself as the “world’s leading cloud software company powering social good.” The clients in question reportedly include, homeless charity Crisis, the UK Universities of Aberystwyth and Aberdeen*, each of which has issued apologetic notices to its customers and partners. Other customers listed by the company include the American Diabetes Association, the Universities of London and Oxford, and YWCA Chicago.
In a statement Blackbaud said: “In May of 2020, we discovered and stopped a ransomware attack. In a ransomware attack, cybercriminals attempt to disrupt the business by locking companies out of their own data and servers. After discovering the attack, our Cyber Security team — together with independent forensics experts and law enforcement — successfully prevented the cybercriminal from blocking our system access and fully encrypting files; and ultimately expelled them from our system. Prior to our locking the cybercriminal out, the cybercriminal removed a copy of a subset of data from our self-hosted environment. The cybercriminal did not access credit card information, bank account information, or social security numbers.”
It went on, “Because protecting our customers’ data is our top priority, we paid the cybercriminal’s demand with confirmation that the copy they removed had been destroyed. Based on the nature of the incident, our research, and third party (including law enforcement) investigation, we have no reason to believe that any data went beyond the cybercriminal, was or will be misused; or will be disseminated or otherwise made available publicly. … We apologise that this happened and will continue to do our very best to supply help and support as we and our customers jointly navigate this cybercrime incident.”
It is not clear from the statement what reassurance was given by the criminals that the data would not be misused or shared in future, or how Blackbaud could trust the hacker’s assertion it was destroyed.
Discovered in May, notified in July
In a message to its alumni, Rob Donelson, executive director of Advancement at Aberdeen University wrote: “On 16 July 2020, Blackbaud advised us that it had discovered a ransomware attack in May 2020. According to Blackbaud, the cybercriminal removed data from its backup server at some point between 7 February and 20 May 2020, and we have been informed that data related to our alumni was part of that. We understand that a significant number of organisations around the world have been affected.”
One point of immediate concern to clients was Blackbaud’s delay in notifying them of the data breach. Aberdeen University said: “Blackbaud has advised that they did not notify us sooner because they needed to: defend against the attack; conduct the subsequent investigation; take measures to address the issue that led to the incident; and prepare resources for its customers. However, we are investigating this further,” adding pointedly, “We are reviewing as a matter of urgency the contractual arrangements with Blackbaud, focusing on their current and proposed security measures for our data. We have also made a formal report to the Information Commissioner’s Office (ICO).”
Could it have been me?
If this can happen to an organisation whose raison d’etre is the storage and protection of mission-critical data then it demonstrates that this could happen to any of us. We would urge readers to spend a few minutes considering how they might benefit from the 5 Steps outlined in the NordLocker article.
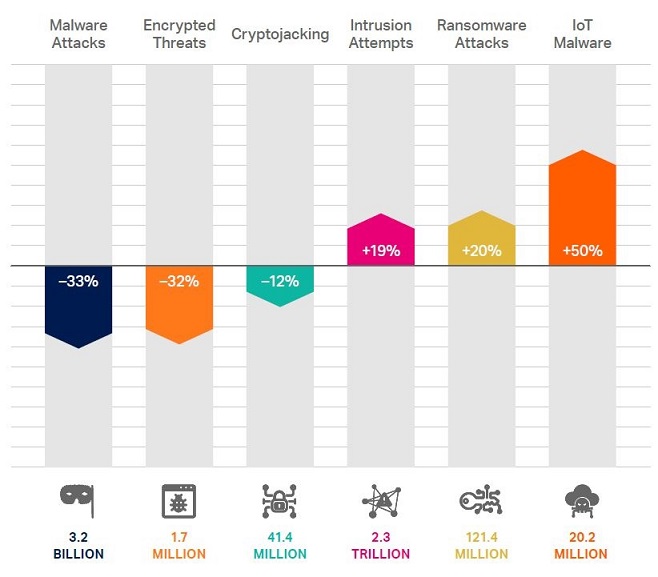
SonicWall’s mid-year Cyber Threat Report
Report finds ransomware up globally
SonicWall Capture Labs threat research team has published its mid-year update to the 2020 SonicWall Cyber Threat Report. This highlights increases in ransomware, opportunistic use of COVID-19, systemic weaknesses and growing reliance on Microsoft Office files by cyber criminals.
SonicWall president and CEO, Bill Conner said, “This latest data shows that cyber criminals continue to morph their tactics to sway the odds in their favour during uncertain times. With everyone more remote and mobile than ever before, businesses are highly exposed. It’s imperative that organisations move away from makeshift or traditional security strategies.”
During the first half of 2020, global malware attacks fell from 4.8 billion to 3.2 billion (-24%) over 2019’s mid-year total. This drop is the continuation of a downward trend that began last November. Despite this decline, Conner said, “ransomware continues to be the most concerning threat to corporations and the preferred tool for cyber criminals, increasing a staggering 20% (121.4 million) globally in the first half of 2020.
Comparatively, the U.S. and U.K. are facing different odds. SonicWall Capture Labs threat researchers logged 79.9 million ransomware attacks (+109%) in the U.S. and 5.9 million ransomware attacks (-6%) in the U.K. — trends that continue to ebb and flow based on the behaviours of agile cybercriminal networks.
Malware-laden COVID-19 emails
The combination of the global pandemic and social-engineered cyber attacks has proven to be an effective mix for cyber criminals utilising phishing and other email scams, according to SonicWall.
As expected, COVID-19 phishing began rising in March, and saw its most significant peaks on March 24, April 3 and June 19. This contrasts with phishing as a whole, which started strong in January and was down slightly globally (-15%) by the time the pandemic phishing attempts began to pick up steam.
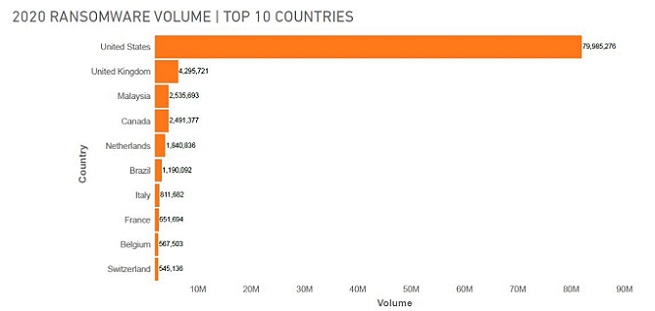
SonicWall Cyber Threat Report
IoT continues to serve threats
Work-from-home (WFH) employees or remote workforces can introduce many new risks, including Internet of Things (IoT) devices like refrigerators, baby cameras, doorbells or gaming consoles. IT departments are besieged with countless devices swarming networks and endpoints as the footprint of their corporate expands beyond the traditional perimeter.
Researchers at SonicWall found a 50% increase in IoT malware attacks, mirroring the number of additional devices that are connected online as individuals and enterprise alike function from home. Unchecked IoT devices can give cyber criminals an open door into what may otherwise be a well-secured organisation, said SonicWall.
To download the mid-year update, go to:
Other cyber security guidance is available on these pages:
www.ncsc.gov.uk/guidance/suspicious-email-actions
www.ncsc.gov.uk/collection/top-tips-for-staying-secure-online
www.equifax.co.uk/resources/identity_protection/how-to-spot-a-phishing-email
www.ico.org.uk/your-data-matters/identity-theft
The author is Jeremy Cowan, editorial director of VanillaPlus, The Evolving Enterprise, and IoT Now.
* For full disclosure, Jeremy Cowan is an alumnus of Aberdeen University, Scotland.
Comment on this article below or via Twitter: @IoTNow_OR @jcIoTnow
Leave a Reply